BOUNTY HUNTER HACK THE BOX WALKTHROUGH
Welcome to tamilcode
HERE IS TRICKS AND TECHNOLOGY
so in this website, we going to see the walkthrough or writeup for bounty hunter hack the box machine and we going to take over the user flag and root flag of the machine...
so first turn and on your hack the box VPN and load the IP address on your browser which is 10.10.11.100
ENUMERATION :
writer hack the box machine
https://tamilcodeoffical.blogspot.com/2021/08/writer-hack-box-walkthrough.html
First, we going to take the Nmap scan using the below command
STEP 1: nmap -sC -sV 10.10.11.100
the result is shown below:
so in this result, we are able to see the interesting services is SSH and port is 22
Next, we going to brute force the directory using gobuster for any interesting directory
STEP 2: gobuster dir -u http://10.10.11.100/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
result for gobuster
so in this gobuster result, we will abe to see the lots of hidden directories...
Next, go to the webpage and click the portal tab in this section you will be able to see the development under construction, and there is a click the here button.
JOIN IN THE MEMBERSHIP
https://tamilcodeoffical.blogspot.com/p/tamilcode-membership-program.html
Click the button it will
further, I have tried more SQL injection but nothing done
SCANNING :
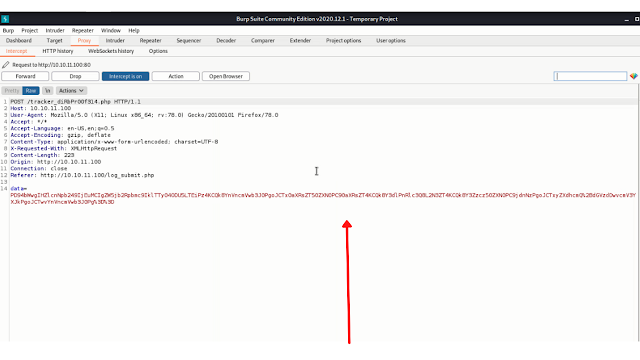
further, I have scanned the webpage using burpsuit (shown in the below image )
And the request to the burpsuit repeater...
In this request, the data is encoded in the url+base64 encoding.
so going to decode the encoding using the cyber chief website (link is below)
we going to decode using this website (instructions are shown below image)
now it has been decoded
And it looks like an XML file and have found that it has XXE vulnerability using the below website...
so in this website, you will be able to study XXE or XML vulnerability...
Now we going to inject the XXE payload in the XML file and encode the file and send it to the web application...
you can download the payload using the below link
Now can able to download the payload and inject in the XML file (image is shown below)
Next, encode a file using cyber chief the encode should be base64+urlencoding (shown below image)
so copy the encode and paste burpsuit data request (show below image)
Now send the request you get a response... in this response, you are able to see some encode (shown below image)
In this encoding you will be able to see the password... but I have tried this username and password it will not work and I have a password for another user it will work by using another payload...
You can able to download the payload using the below link
Copy the payload and paste it into the XML file and encode the XML file by seeing the below image...
I hope you will understand this article please subscribe my website and please support us by donating using the below link




















how do you got path tracker_diRbPr00f3l4.php ??
ReplyDeletepayload download nahi ho raha he ??
ReplyDeleteHello, excuse the question but recently they have changed the key of this virtual machine, I already decrypted it but when I enter it, it bounces me wrong
ReplyDeletePost a Comment