PRIVILEGE ESCALATION SERIES 1
WELCOME TO TAMILCODE
HERE IS TRICKS AND TECHNOLOGY
WHAT IS TRYHACK ME?
Tryhack me is a platform for learning hacking especially for beginners ... you can
learn a lot from the try hack me if want go to website please click the below link
WHAT IS PRIVILEGE ESCALATION?
Privilege escalation is nothing but changing the user privilege access to root/admin
privilege... there are more ways for privilege escalation ...
FOR AN EXAMPLE :
you have compromised the windows / Linux machine
in this case, now get spawn shell. so in this shell, your only normal user now get to change root/administrator by finding password or vulnerability in the machine so is called
privilege escalation...
simply we can say change user access to root/administrator access
now somebody asks how?
by finding the vulnerability or bug or security flaw...
there are two types of privilege escalation
1. horizontal privilege escalation
2. vertical privilege escalation
Horizontal privilege escalation :
Now let image ... you get the shell in the web application which is
www-data ------> if it is normal user shell which /home/user ---> then this called horizontal privilege escalation .....
Vertical privilege escalation :
now let image .. you get the shell in the web application which is www-data ------> if it is
root shell which /root -----> then this called vertical privilege escalation ...
now in this series, we going to see only for Linux privilege escalation in try hack me
so there are Linux privilege rooms you can also sign up and get into it ...
LINUX PRIVILEGE ROOMS :
Weak permission
etc/shadow
shadow is a file in which the password is stored in a Linux machine .....
world-readable :
world-readable which we can read the file symbol is (r)
world writeable :
world writeable which can write into file symbol is (w)
HOW TO FIND WORLD-READABLE AND WRITEABLE?
open the terminal use the below command
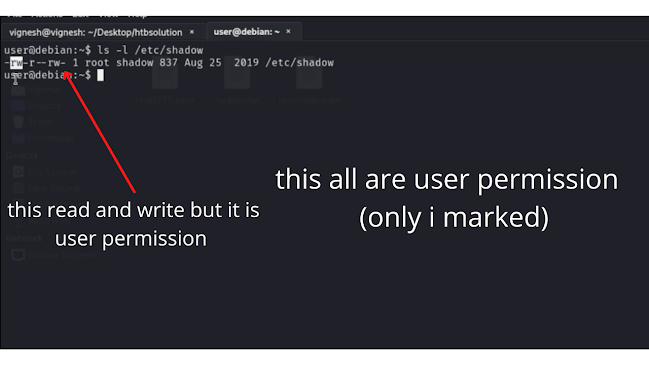
CMD: ls -l /etc/shadow
now get something shown in the below image
by seeing the above image...
in the center there (r) -----> which is the root
in the left side ( rw ) ---> which world readable and writable (permission only for root )
( permission for normal user )
by seeing the above image
in the right side ( rw ) ---> which word readable and writable ...
now you can clearly understand world-readable and writeable ..........................
now get into try hack me machine ...................
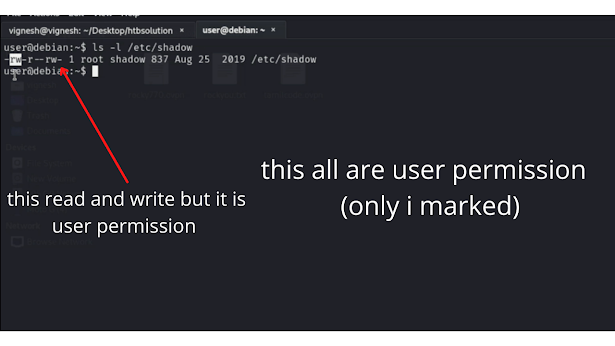
give the command of ls -l /etc/shadow.
now it will show (rw) which world-readable and writeable ( right side )
Waring :
see it clearly not left side (root) only right side ( user permission )......
WHAT ARE THE POSSIBILITY (WORLD-READABLE )?
in this case, you can able see read the hash and crack to find the password ...
now you copy the root hash and save the hash in your machine use john to crack the
password .........
CMD: john hash.txt -w /home/user/worldlist
in the -w denote wordlist in your machine .................
now you get the password of the machine .......................................
WHAT IS THE POSSIBILITY (WORLD WRITEABLE )?
In this case, you can overwrite the hash ... so first identify the hash using hashid
tool
CMD:
hashid '$6$Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET..it8r.jbrlpfZeMdwD3B0fGxJI0'
you won't give only a single quote to identify the hash ............
now you will able to identify the hash which is SHA-512 crypt
now we going to create the password in the hash type using mkpasswd
CMD: mkpasswd -m SHA-512 test
you type any name in the test place...
now you get a hash copy the hash and paste in victim machine .......
now exit from the ssh connection and make another connection new ............
now type su and password what your given and I give test so I enter the test now
it gets login ...............................
so this possibility to enter into the machine ... so I am saying possibility because more
beginner seeing this website..... it is only demo for privilege escalation is not answer for tryhack me .. it just to change the user access to root access using the weak permission..
if like our work and articles please donate for me to develop more thing and it
support me to write more articles ..............................
VIDEO ....................................





Post a Comment