MITIM ATTACK OVER THE ETTERCAP
WELCOME TO TAMILCODE
HERE IS TRICKS AND TECHNOLOGY
BEFORE THAT STUDY ABOUT MITIM ATTACK USING BELOW LINK:
https://tamilcodeoffical.blogspot.com/2020/12/hi-welcome-to-tamilcode-so-in-this.html
SO IN SESSION, WE GOING TO DISCUSS WHAT IS ETTERCAP? AND HOW TO USE IT? AND TO PERFORM THE MITM ATTACK USNG ETTERCAP ETC ...
WHAT IS ETTERCAP?
Ettercap is a free open-source network security tool. and it is used for computer network protocol analysis and security audit ...it special designed for MITM attacks in LAN network
- MITM = MAN IN THE MIDDLE ATTACK
- LAN = LOCAL AREA NETWORK ...
- it was developed in a c programming language
- it will support Linux , Windows , MAC os
USE OF ETTERCAP?
- it used to perform the MITM attack
- ARP poisoning
- used to scan the host
- sniffing
- DOS ATTACK ( denial-of-service)
HOW TO PERFORM THE MITM ATTACK?
WARNING:
NOW I'M USING THE KALI LINUX MACHINE !!!!
..............................................................................................................
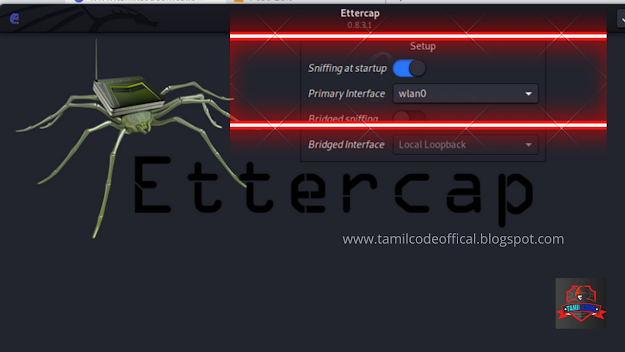
STEP 1: turn on your ettercap using the command of ettercap -G or open by the searching tool in kali linux menu ...
STEP 2: check whether starting sniff it on and choose the primary interface is wlan0.
default on in ettercap if it is off please on in ettercap otherwise Your sniffing is not work in a tool .....
STEP 3: stop sniffing .. or see the below picture to stop the sniffing.
STEP 4: Before starting our sniff we going to setup some modules in the ettercap tool.
STEP 5: so first going scan host for our target ... click the ettercap menu and click hosts so there hosts list click that ( see below picture)
STEP 6: by seeing the below picture the IP address and MAC address is shown in the scan section
STEP 7: now add the IP address in target 1 to attack.
STEP 8: so next start our sniffing by clicking the start button in ettercap and click the MITIM menu there is an ARP poisoning.
STEP 9: click the ARP poisoning and tick the sniff remote connection option .....
STEP 10: Now we add the victim to our target.
STEP 11: so when the victim opens any login page of the website
we get his sensitive credential
STEP 12: below see the below image we got username and
password
now the username = test and password = test
I HOPE YOU WILL UNDERSTAND THE ARTICLE SO PLEASE SUBSCRIBE MY CHANNEL TAMILCODE AND MY WEBSITE THANKS FOR LEARNING HERE ......
WATCH OFFICIALLY :
FACEBOOK LINK :
WEBSITE LINK :
IF YOU LIKE THE ARTICLE PLEASE SUPPORT US BY BUY ME A COFFEE ....
BUY ME COFFEE LINK ONE :
BUY ME COFFEE LINK TWO :












Post a Comment